| |
No Drive Letter in the Windows Explorer |
Drive Letter hidden
Windows can be configured to hide drive letters in the Windows Explorer. The settings can be made with
Microsoft TweakUI under My Computer -> Drives. Or download and execute this reg file:
explorer_nodrives_0.reg
TrueImage 2009
TrueImage 2009 Home may prevent Windows from assingning drive letters to removable drives. An update to "Build #9615" fixes this.
Drive Letter Conflict with Network or Subst Drives
Since XP Network and Subst drives are no more global, they exist in the context of the user who created them only. In the context 'System' where the Mount Manager assigns drive letters such drives are not visible offhand. Therefore they are not considered by XP. If there is a network drive on the first available local letter then XP assigns it again to a new external drive. The external drive is invisible and unaccessible then until its drive letter is changed in the Disk Management (right click My Computer -> Manage -> Disk management) or by my commandline tool ReMount. But for each new drive you have to change the drive letter again and it's no solution to assign a letter again to a different external drive because XP can save exactly one assignment per letter.
So change the network drive's letter to a higher one to get the lower ones available for external drives. Or let my USB Drive Letter Manager change the letters of USB drives for you.
Microsoft is aware of this and calls it
a problem. Meanwhile a hotfix is available (WindowsXP-KB297694-x86-ENU.exe) and the XP Service Pack 3 fixes the problem too.
What the SP3 did not fix is this scenario: Letters C: + D: used for local drives, E: for a USB drive.
Remove the USB drive, create a network drive at E: and reattach the the USB drive again. XP with SP3 will assign E: anyway, the USB drive is 'hidden'. This is fixed in Vista.
Another hotfix shall fix this for XP too: http://support.microsoft.com/kb/961187
The problem persists when an external drive is attached before the user logs on. The mapping of the network drives fails when their drive letter is in use. USBDLM fixes this when configured appropriate.
New external drive not partitioned
New external drives are often unformatted and unpartitioned. Partitioning can be done in the Windows Disk Management (right click My Computer -> Manage -> Disk management) or
see here.
Windows Server 2003
Windows Server Enterprise and DataCenter Edition do not assign drive letters to new fixed drives (USB and Firewire disks are usually 'fixed'). This is up to the administrator because otherwise SAN (Storage Area Network) drives might be mounted accidentally.
This feature is called AutoMount and can be enabled by means of the DiskPart tool: Open a commandprompt, enter diskpart, on the DiskPart prompt enter automount to see the current state or automount enable to enable it.
Or install my USB Drive Letter Manager which can assign a drive letter for USB and firewire harddisks without affecting other types of storage devices.
Drive encrypted
Some flash drives and external harddrives come with an encryption software. Usually you have the option to split the drive into an unencrypted and an encrypted part. The unencrypted part appears on all computers but the encrypted part becomes visible and/or accessible after you entered a password when the encryption software asks for. But of course this happens only when this software is installed on the computer you attach the drive to.
Daemon Tools V4
There are reports that a more or less failed installation of the Daemon-Tools V4 makes XP fail assigning drive letters to new drives.
It's suggested then to uninstall the tools and to delete some files in System32\Drivers: sptd.sys, secdrv.sys, sptd.sys, sptdNNNN.sys (NNNN = numbers). Here are some more information:
http://www.daemon-tools.cc/dtcc/archive/index.php/t-7868.html
For the deinstallation there is
sptdinst_x86.exe.
Recently there are no more reports about this issue, the problem seems to be fixed.
Filter Drivers
Filter drivers are used to manipulate the communication between soft and hardware. They are installed for instance by CD burning software (device class CDROM), by anti virus software (device classes DISK, CDROM and FLOPPY) or by virtualization software as VMware for making USB devices availlable in the virtual machines (device class USB).
Especially after Windows updates some detail may have changed which make a filter driver fail.
The references to the filter drivers are found in the Registry under
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Class\{GUID}. GUID is an 'Global Unique Identifier', something like {4D36E967-E325-11CE-BFC1-08002BE10318}.
The GUIDs mentioned above are:
| GUID_DEVCLASS_DISKDRIVE | = {4d36e967-e325-11ce-bfc1-08002be10318} |
| GUID_DEVCLASS_CDROM | = {4d36e965-e325-11ce-bfc1-08002be10318} |
| GUID_DEVCLASS_FLOPPYDISK | = {4d36e980-e325-11ce-bfc1-08002be10318} |
| GUID_DEVCLASS_USB | = {36fc9e60-c465-11cf-8056-444553540000} |
On a fresh installed Windows the only filter driver is under GUID_DEVCLASS_DISKDRIVE the value UpperFilters with "PartMgr". No others are there under the GUIDs mentioned above.
Found filter drives can be explored under C:\Windows\System32\drivers to identify the software which has installed it.
A filter driver can be deactivated by renaming the UpperFilters or LowerFilters value. Then restart Windows.
Digital Camera
Digital Cameras use either the USB Mass Storage Protocoll or the Picture Transfer Protocol (PTP). With the latter one there is no drive letter. For getting a drive letter a 3rd party software is required, as PTPdrive: http://www.ptpdrive.com ($29 USD).
Other 3rd party software
Anti virus, anti spyware, anti anything, personal firewalls, cd/dvd writing software, the Adobe download manager, Symantec NetBackup, usually installs a service and some drivers to get as much control as possible. Sometimes such services and drivers cause very strange effects.
In the U3 FAQ there are some hints for U3 sticks but some may be true for normal flash drives too.
To discover if a problem is caused by 3rd party software first start XP in Safe Mode. If the problem is gone then, boot again normal. Go to Start -> Run, msconfig, Tab 'Services',
check 'Hide All Microsoft Services'. Disable them all, reboot and check if the problem is gone again. If yes, then enable them one by one (reboot each time) until the problem is back again. The you have the culprit...
If deactivating services doesn't help, try it with drivers. Start -> Run, devmgmt.msc. View -> Show hidden devices. Open in the device tree 'Non-Plug and Play Drivers'. Here you see lots of items, many from Microsoft and others. You can deactivate a driver by right clicking it an select 'Deactivate'.
If you are not sure about a driver, just enter its name at Google and you will see...
Create a restore point before!
|
|
| |
|
| |
Restricted users are not allowed to eject a media |
Under XP restricted users are not allowed to eject a media from a 'removable' drive (right click on the drive in the Windows Explorer -> Eject). 'Eject' is the right choice to prepare a card to be taken out of an internal card reader. 'Prepare for safe removal' removes the whole device...
Ejecting rights can be changed by a policy:
Control Panel
Administrative Tools
Local Security Policy
Local Policies
Security Options
Devices: Allowed to format and eject removable media
Select 'Administrators and Interactive Users' here. Or doubleclick this REG file:
AllocateDASD2.reg.
After next logon restricted users can eject a media from a drive.
Earlier tests showed that this has no effect, later tests under XP-SP2 patch level april 2007 where successful.
|
|
| |
|
| |
No files larger than 4 GB |
USB flash drives are shipped FAT or FAT32 formatted. Both file system are unable to store files larger than 4 GB (232 Bytes).
For larger files the modern NTFS is required. Getting a USB removable drive formatted with NTFS is a bit tricky, see here.
Take care: Formatted with NTFS USB removable drives get a write cache! The policies for "Write caching and Safe Removal" have no effect on USB removable drives.
So, always use either "Eject" or "Safely Remove Hardeware" to prevent loss of data.
|
|
| |
|
| |
Access Denied on NTFS drives |
If you have formatted a drive with the NTFS file system then you have to deal with access right.
Files and folders put by an admin on the drive can be written and deleted by admins only.
To make all files and folders accessible to everyone you can use the CACLS command like this:
cacls X: /T /G Everyone:F
Replace X: with the right drive letter and Everyone with the correct group name which is depends on your Windows language. "Everyone" works on english Windows, "Jeder" on a german etc...
Of course only an admin can do this.
|
|
| |
|
| |
Increasing Drive Letters |
When USB drives gets new higher letters each time they are attached then a foreign software screws up the system. There are reports that a software called 'Spyware Doctor' causes this effect. Uninstalling should fix it.
Since some month there are no new reports about this issue, the problem seems to be fixed.
|
|
| |
|
| |
Scan and fix under Vista and Windows 7 |
When a FAT formatted "removable" USB drive is attached then under Vista and Win7 the "Scan and Fix" dialog is often shown. This happens when a certain bit in the drive's boot sector is set. It is found in a value with the very meaningful name "BS_Reserved1", see Microsoft's FAT32 File System Specification: fatgen103.doc.
As far as I have discovered, Windows sets the bit whenever a file size is changed and when a file is created or deleted.
Here is my dirty bit watch tool: WatchFatDirtyBit.zip.
It is set back to 0 about 1.5 Seconds after a file size change but very long 30 Seconds after a file was deleted or created without writing data (which does no happen in real live).
Having a write cache active or not seems to have no effect on the dirty bit handling.
So, if you delete a file on a FAT formatted USB drive and remove it within 30 Seconds then you have set dirty bit.
Just always use "Eject" or the "Safely remove hardware" facility, this flushes all data and sets the bit back to null.
|
|
| |
|
| |
Drive letters of CD-ROM drives revert |
When the drive letters of CD-ROM drives revert to a default after every reboot, then we have to deal with the 'ZoneAlarm problem'.
The fix is to uninstall ZoneAlarm, change the drive letters, reboot and install ZoneAlarm again. But there are other reports that the drive letters revert again then. The problem exists since V6.5. The old V6.1 is still
available for download.
There are reports that V6.5.737 fixed the problem too. Others reported the problem with V7.x..
The Nokia Suite 7.x is reported to cause this too.
Another suspect for this problem seems to be Norton GoBack.
|
|
| |
|
| |
USB drive appears to be write protected |
1.
Check out if the USB drive has a small swich for write protection.
2.
Windows can write protect USB drives too. Check out the registry under
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\StorageDevicePolicies.
The value 'WriteProtect' should be absent or set to '0'.
3.
Flash memory has a limited lifetime of about 100000 guaranteed write cycles. Most flash cells life much longer but cells that become defective must be replaced by reserve cells (bad block management). The flash controller manages this in the background. When all reserve cells are consumed then the flash controller rejects all write accesses. Then you can read your data and bring the device the recycling.
This can happen even the drive was never even nearly completely filled because the flash controller spreads write accesses over all physical blocks to ensure that all cells are weared out equally (wear levelling).
Unfortunately USB flash drives have no standard mechanism for reading their current health state as known from harddrives. So, always expect a USB flash drive to die at any time...
|
|
| |
|
| |
Insert a disk |
USB flash drives usually preted to have a removable media (like a card reader). Therefore Windows presents them as "removable" drives. If a flash drives reports a size of zero then Windows comes up with a "Please insert a disk" message because it thinks that this is possible...
But some USB pen drives are indeed little card readers! Therefore it is worth to try to break up the drive to have a look inside. What a pleasure if an SD card is found as here in this ExtreMemory Nano.
|
|
| |
|
| |
USB devices detected as 'unknown device' |
If USB devices worked fine and then suddenly turned into an 'unknown device' then it might be caused by a power management problem. The power management can be deactivated for certain or all USB controllers:
http://support.microsoft.com/?scid=kb;en-us;895962
The USB controller might getting old and just does not work as perfect as when it was new...
On USB flash drives it's reported that their quarz crystal gets defective. If a USB drive shows the same symthoms on several computers, exchanging the crystal is something to try.
|
|
| |
|
| |
XP asks for drivers |
XP comes with drivers for USB mass storage. If it asks for drivers then it cannot find them...
Where to search for drives is stored in the registry. Start the Registry Editor (Run -> Regedit). Check if under HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion the value 'DevicePath' points to '%SystemRoot%\inf'. Additional items, separated by semikolons, are ok but '%SystemRoot%\inf' has to be one of them. Screenshot
Then delete the file C:\WINDOWS\inf\infcache.1 - XP will recreate it.
The INF folder and the infcache.1 file are 'hidden'. To see them in the Windows Explorer:
Menu 'Tools' -> 'Folder Options'
Tab 'View', mark 'show hidden files and folders'
If it still doesn't work after a restart, the files in C:\WINDOWS\inf might be corrupt. An Windows repair install helps then.
Another thing to check is if the values 'FactoryPreInstallInProgress' and 'AuditInProgress' are set to '1' under
HKEY_LOCAL_MACHINE\SYSTEM\Setup
and
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Factory
.
They should be 0 or non present.
|
|
| |
|
| |
Vista asks for drivers or just want to install new hardware |
Here the same is true as for XP. Furthermore Vista seems to tend to loose the files USBSTOR.INF, USBSTOR.PNF and other USBxxxx files from C:\Windows\INF. Probably there are more files missing then, but the USBSTOR files are most frequently used ones.
There are copies of the files in C:\Windows\System32\DriverStore\FileRepository - just copy them to C:\Windows\INF.
|
|
| |
|
| |
You must be a member of the administrators group |
When XP comes with the "You must be a member of the administrators group to install ..." logon dialog, then Windows does not trust its own drivers or other involved files.
This is the case when it cannot check if the drivers are digitally signed which is true when the service 'Cryptographic Services' is not running (CryptSvc) or if its data are corrupt.
Start -> Execute -> services.msc
Check here for 'Cryptographic Services' being started automatically.
Next thing to check is the log file C:\Windows\setupapi.log. Failed digital signatures of drivers or other involved files are logged here.
Furthermore XP comes with a tool to verify the signatures of all files. Start -> Run, enter sigverif here.
If you have found the problematic file, check its file version and try to get a replacement with the exact same version from another computer or do a repair installation.
Another possible reason is a corrupt database of the 'Cryptographic Services'. How to fix this is described at Microsoft:
http://support.microsoft.com/kb/822798
The symptoms described there are different, but the cure is right.
|
|
| |
|
| |
USB drive not working stable |
When a USB drive makes problem on one computer only then an updated mainboard/chipset driver may help.
If it doesn't help then it may be just incompatible with the computer's USB ports - that's not unusual. Therefore it's helpful to have an additional USB PCI card as alternative in the computer, best with NEC chip.
Cheap USB extension cables may cause problems too. The thinner and longer the higher the risk for problems. The plugs wear out in time.
USB ports on front of the computer are more problematic because the USB is leaded by a cable thru the computer case which is full of interferences. Furthermore the port a mechanically stressed, so the usually fail sooner or later.
Other attached USB devices may interfere, usually such ones that don't use a default Windows driver and which permanently transfer data, such as web cams.
Cheap USB hubs die slowly. First symptoms are disappearing devices and communication freezes.
Another try is a complete USB device clearing by Microsoft
DEVCON and the RenewUSB.bat from
http://www.robvanderwoude.com/devcon.html
Under x64-Windows Microsoft's devcon.exe does not work, an x64 version is required. This one is ok:
http://www10.zippyshare.com/v/12721641/file.html
To make the devconx64.exe work with the RenewUSB.bat rename it to devcon.exe and put it into the same folder.
A cleanup can be done manually too. Put the following two lines into Notepad and save them as DevManager.CMD:
set DEVMGR_SHOW_NONPRESENT_DEVICES=1
devmgmt.msc
Started thru this DevManager.CMD the Windows device manager shows non present devices too if you check "View" -> "Show hidden devices". Since Vista this must be started "As Administrator", otherwise it has no effect.
Under "Disk drives", devices shown with a light gray icon are non present. Just delete them. Same procedure under "USB Controlers" and "Storage volumes". There may be a lot of them...
My commandline tool DriveCleanup does it for all currently non present storage volumes and USB drives.
Microsoft has set up a page for
General USB troubleshooting in Windows XP
To have DEVMGR_SHOW_NONPRESENT_DEVICES=1 set permanently, download and doubleclick this file:
DevMgr_Show_1.reg. After next logon it takes effect.
It also sets DEVMGR_SHOW_DETAILS=1 to get the "Details" tab in the device's properties dialog under XP-SP1.
|
|
| |
|
| |
Data loss when certain occupancy level reached |
When a USB flash drive causes errors when it reaches a certain occupancy level then it's probably a fake which has a fraction of the promised capacity only.
Written data then either overwrites data on other addresses or are just lost in space. Therefore formating with NTFS fails while FAT works because the NTFS file system is written into the middle of the drive.
You can check suspicious and new drives by means of free tools:
If a drive is a fake then you can create a small partition to protect the non existing range from being used.
Windows 2000, XP and higher do not support creating partitions on removable drives. Here the EaseUS Partition Master is helpful. Or do it under Linux or by means of the Ranish Partition Manager.
|
|
| |
|
| |
Format a USB drive |
If the Windows Explorer fails to format a removable USB drive then one of these tools may help (for removable drives only):
HP USB Disk Storage Format Tool
SD Memory Card Formatting Software
RMPrepUSB
Some more tools
USB Boot Making Applications
To test if there is any access to the drive, you can use
Hex Workshop.
'Disk' -> 'Open Drive...'
Select here the drive by its size. Stop here if you are not sure!
Once opened it shows the content of sector 0 where you find the partition table on harddisks. On removable drive there can be a partition table or a boot sector ('super floppy').
The format tools mentioned above all write a partition table. XP creates super floppies on new medias.
To give a disk a complete new start, just overwrite sector 0 with zeros: In Hex Workshop select all using the mouse, click '&', OK, save. Now you can go to the disk management console to partition and/or format the drive again.
FAT32 on drives > 32 GB
Under XP and higher Microsoft has blocked formating drives larger than 32 GB with FAT32 without a good reason. But for devices with a standalone function as image tanks or MP3 players FAT32 is essential - they don't work with NTFS formatted drives.
The german computer magazine c't offers a format tool -
H2Format. But it works on unformatted partitions only. To prepare a drive, go to the Disk Management, delete the partition, create a new one and select 'Do not format'. Then use H2Format to write a FAT32 file system - usage is similar to the FORMAT.EXE. Sample:
h2format u:
It's very fast because it does nothing else then writing an empty FAT32 file system.
Another FAT32 formatting tool is
Fat32Formatter.
Under Linux there is the tool "MakeDosFileSystem", short MKDOSFS. There is a Windows port:
http://www1.mager.org/mkdosfs
A modern BIOS sees USB drives (at least a single one), so you can deal with them under pure MS-DOS too. Or without any operating system: Get the great
Ranish Partition Manager, unzip it, start the PART.EXE under Windows. It detects that it's running under Windows and offers the option 'Copy PART.EXE and update boot sector on A:'. This writes the program to a floppy in drive A: that you can boot from then. It does not contain an operating system but it's bootable.
| |
| |
|
| |
On flash drive only the first partition works |
Nearly all USB flash drives pretend to have a removable media (even it's a lie), so Windows detects them as 'removable'. On drives with a removable media Windows 2000 and higher supports only one partition.
Large USB 3.0 Flash Drives are sometimes SSDs in fact. They are usually detected as fixed drive, e.g. the great Sandisk Extreme.
Finally it's a single bit in the device's device descriptor, the removable media bit (RMB). If you take away the RMB then Windows sees the drive as 'local disk' and multiple partitions work.
The Removable Media Bit can be changed either in the drive's hardware or by a Windows filter driver.
Changing in the hardware works with some flash drives by means of the tool
Lexar BootIt.
Flash drives which has been successfully turned into fixed drives (the internal hardware may change, so you never know...):
- Corsair Flash Voyager 8 GB (VID_090C&PID_1000)
- Corsair Flash Voyager 16 GB (not VID_1B1C&PID_1AB1)
- Corsair Flash Voyager GT 4 GB (VID_1B1C&PID_1A90)
- Corsair Flash Voyager GT 16 GB (current devices don't work anymore)
- Corsair Flash Survivor 32GB
- OCZ Rally2 32 GB
- OCZ Rally2 Turbo 8 GB
- OCZ ATV 4GB
- Buffalo Firestixx 1 GB (RUF2-S)
- Buffalo Super High Speed USB Flash Type R 8 GB
- Super Talent Pico-C Chrom 8GB (current devices don't work anymore)
- Intenso USB Drive 8 GB Slim Line
- Sony Tiny Vault 2GB
- LG USB Drive 2 GB (UB2GVMS01)
- Ativa 325-300 16GB
- PQI Intelligent Drive i820 4 GB (8 GB does not!)
- Powerram mini Pro (16GB)
- Verbatim 4 GB Store' n Go
- Sony Micro Vault 8 GB
- Lexar JumpDrive TwistTurn 4GB (LJDTT4GB) (Mid 2012)
- ATP Nano Vision (4GB) (April 2013)
All these flash drives must have something in common, probably the vendor of its controller chip. Since the vendor ID is obviousely freely configurable by the OEM, some drives must be opened to give us a look at the chip...
Since some years no more devices are reported to work with the Lexar-Tool. Problably the controller chip is not more in production.
Update: The last one (Lexar JumpDrive TwistTurn 4GB) was reported in 2012, so it might be available.
A Transcend JetFlash 600 16GB is reported being destroyed by the Lexar-Tool...
A filter driver for removing the RMB has been made by Hitachi for their Microdrives (Compatct Flash cards with a mini harddrive):
xpfildrvr1224_320.zip
It is 32 bits only, so it will not work on x64 editions of Windows.
By modifying the included INF file the filter driver can be used with any other 'removable' drive.
For the device detection there are the lines in section [cfadisk_device]:
[cfadisk_device]
%Microdrive_devdesc% = cfadisk_install,IDE\DiskIBM-DSCM-11000__________________________SC2IC801
"IDE\DiskIBM-DSCM-11000__________________________SC2IC801" is the device ID of one of the supported Microdrives.
In analogy to these lines we add one line for each 'removable' USB drive we want to turn into a USB hard drive. The ID is found in the Windows device management: Expand 'Disk drives', right click your USB drive, select Properties. On the tab "Details" under XP the item "Device instance ID" is already selected. Click on the ID in the List and press Ctrl+C, this copies the ID into the Windows Clipboard and can be pasted somewhere else with Ctrl+V.
XP up to SP1 shows the tab "Details" only when the environment variable DEVMGR_SHOW_DETAILS=1 is set:
DevMgr_Show_1.reg download and doubleclick the file, then relogon to take effect.
Sample:
USBSTOR\DISK&VEN_LEXAR&PROD_JUMPDRIVE&REV_1.30\K326441127040&0
We need the fat part:
[cfadisk_device]
%Microdrive_devdesc% = cfadisk_install,USBSTOR\DISK&VEN_LEXAR&PROD_JUMPDRIVE&REV_1.30
Or much more simple the universal way for any USB disk:
%Microdrive_devdesc% = cfadisk_install,USBSTOR\GenDisk
In the last line of the INF file we change "Hitachi Microdrive" into something nice as "RemovableToFixed".
In the device manager again right-click the USB drive, "Update driver...", then "No, not this time" -> Next -> "Install from a list or..." -> Next -> "Don't search." -> Next -> "Have Disk" -> browse to the INF file here. Now "RemovableToFixed" should be in the list -> Next -> Confirm the two warnings -> Finish.
Now the drive is redetected, actually as USB hard drive. The drive can be partitioned, the policy "Optimize for performance" indeed activates a write cache on FAT formatted drives and Windows will create the beloved folder "System Volume Information"...
My tries to automat the installtion by means of Microsoft DEVCON did not succeed.
The filter driver can be removed by deleting the drive in the Windows Device Manager. After reattaching the drive its drivers are installed again, but not the filter driver.
|
|
| |
|
| |
Remove non removable drives from the "Safely remove hardware" list |
Internal card readers of desktop PCs are usually USB devices. The USB standards define no mechanism which allowes a device to say "I'm internal and not removable". USB hubs can mark ports as 'non removable' but I have never seen a root hub doing so. I have seen an internal hub of an USB flash drive which has marked his ports as 'non removable' but this had no effect on Windows' behaviour.
So, obviously internal USB card readers are always listed in the "Safely remove hardware" facility.
There are also SATA drivers which pretend their internal drives being removable.
As far as known devices are shown in the "Safely remove hardware" list if they are marked as removable and
not as "surprise removal is ok".
These are bit coded flags:
From cfgmgr32.h:
#define CM_DEVCAP_REMOVABLE (0x00000004)
#define CM_DEVCAP_SURPRISEREMOVALOK (0x00000080)
The device capabilities are found in the registry in a value
named 'Capabilities' under (sample for a USB drive):
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Enum\USB\Vid_090c&Pid_1000\A740000000000097
If you take away 4 from the value or add 80h and then refresh the safe removal dialog by toggeling the checkbox, then the drive is gone.
But the value is reset when you attach the drive for the
next time or on next boot. This is hard coded into the driver
and read each time the drive is loaded. If you export the modified
value into a reg file then you can silently load it on startup like this:
regedit /s hidecardreader.reg
But you need admin previleges to write this value. Under Vista even an admin is not allowed to change the value offhand.
In Windows 7 the safely remove hardware facility can do both, 'safely remove' and 'eject'. So, even with the modification, 'removable' drive will not disappear from the list, but only eject is available.
The device instance id string of your drive (this USB\Vid_090c&Pid_1000\A740000000000097 thing) is found in the
properties of the drive in the device manager on the 'Details' tab. But XP shows the tab "Details" only when the environment variable DEVMGR_SHOW_DETAILS=1 is set:
DevMgr_Show_1.reg download and doubleclick the file, then relogon to take effect.
On the tab "Details" under XP the item "Device instance ID" is already selected. Click on the ID in the List and press Ctrl+C, this copies the ID into the Windows Clipboard and can be pasted somewhere else with Ctrl+V.
Meanwhile I've added a function to do this to my USB Drive Letter Manager, see USBDLM help.
|
|
| |
|
| |
USB serial number |
USB devices should have a hardware serial number which is unique for each exemplar. But there are lots of devices which have no serial or where all exemplars have identical serials.
This results in different behaviour when a different USB port or another exemplar of the same USB device is used.
| |
USB Port is changed |
USB device is changed |
| no serial |
detected as new |
detected as the same |
| unique serial
|
detected as the same |
detected as new |
| all indentical serials |
detected as the same |
detected as the same |
The only way to change the behaviour is to make Windows to ignore the serial. This can be done for all USB devices or for a certain device. See below.
Two identical drives
Two identical drives doesn't work if they have identical USB hardware serial numbers. This is a violation of the
USB mass storage specs but such drives exist. As far as I've seen such drives can be used alone only.
Some say that the sentence 'If provided, the serial number must be unique to each USB
Vendor ID and Product ID pair.' can be interpreted as allowing the same devices from the same manufacturer to have the same serial number, albeit unique to that product line from that manufacturer, but I think the term 'serial number' alone makes absolutely clear how to read that.
You get what you pay for. Giving each device a unique serial costs some cents,
while omitting the serial make the users complain about the device
being detected as new one when it's attached to a different USB port...
Update: I've tested two USB single slot card readers with identical USB serials: XP-SP2 fully patched and Vista where able to handle this at least on first view. They handle the second drive similar to drives without a serial. But I've also seen an XP which generates a blue screen when the second device is attached...
You can check the USB serial by means of my commandline tool ListUsbDrives, for other USB devices there is the Microsoft demo project "USBView" but Microsoft does not offer executables for download. Therefore I've made a tool based upon Microsoft's USBView sources: UsbTreeViewer.
Windows 2000 and higher can be forced to ignore all USB serials or the serial of devices specified by vendor and product ID:
Under
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\UsbFlags]
there is (up to XP) the value GlobalDisableSerNumGen:
0 disable all USB serials
1 enables USB serials
On first view the name seems to implicate the opposite. Probably DisableSerNumGen stands for Disable Serial Number Generation, so when 'Generation' is disabled then the real serials are used.
Since Vista the value no not present by default. Just create it as new binary value.
The better solution is an individual setting for the device in question.
Windows 2000, XP: Create an entry under the above key. The name starts with "IgnoreHWSerNum" followed by the vendor and product ID of the device. The value for ignoring the serial is 1 as the name implies.
Example for vendor=1111 and product=9999:
IgnoreHWSerNum11119999=1
The value should be a binary and have exactly 1 byte.
For USB drives you can get the IDs by means of my ListUsbDrives started with parameter -a (all drives and informations):
You find them in a line like this
Ctrl ID = USB\VID_1111&PID_9999\USB_serial_number
For any USB device you find the USB hardware ID in the Device Management in the device's properties in the "Details" tab.
No restart required to take effect.
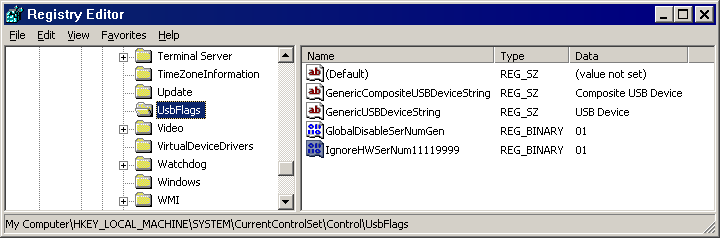 RegEdit with GlobalDisableSerNumGen and IgnoreHWSerNum11119999
RegEdit with GlobalDisableSerNumGen and IgnoreHWSerNum11119999
Vista, Win7, Win8:Here Windows create under UsbFlags for each USB device an 12 digit key with the format VVVVPPPPRRRR (Vendor, Product, Revision), just find the right one. Below create a DWORD value with 1. At least that's what Microsoft says . Here I have seen no effect under Win7.
Ignoring the serial can be used to prevent the plug and play is triggered when a USB device is exchanged by another expemplar of the same model. This is great for instance when a USB printer is defective and replaced. When the serial is ignored (or not present) the new printer just works as long as it's connected to the same USB port.
|
|
| |
|
| |
USB device stays powered after safe removal |
In contrast to XP under Vista and Windows 7 USB devices stay powered after performing a safe removal. Microsoft says this is for being able to charge mobile devices even they are safely removed...
But this new behaviour can be turned off by means of the registry value "DisableOnSoftRemove", see here: http://support.microsoft.com/kb/2401954
|
|
| |
|
Counter since Feb. 1998

last change: 12 April 2013
Uwe Sieber
Home |